📚 Digital Spheres of Privacy | Evaluating Tech Security
Part II: Radicalizing Our Tech Stack for Resilience
Hey y'all, welcome back! 👋🏼
With Big Tech sitting firmly in the White House, I want to offer a very practical guide to securing you and your organization's digital privacy. Today, I offer how to assess your risk and security needs. Read on for more...
In Case You Missed It:
📚 for communicators: 📚 (Cyber)Securing Our Futures Identities, & Organizations
🌱 for activists: 🌱 Hollywood's Reflections on Society
Digital Spheres of Privacy
Part II: Radicalizing Our Tech Stack for Resilience (Parts I, II, III, & IV)
When major historical events happen (as they seem to do frequently these days!), there is a moment where the earth quakes and it feels we are stepping into a new era of history that won't be like the last. Now that we're on the other side of the election, however, life seems to keep moving along and offering the semblance of normality. Despite that, we still need to prepare for a less secure future ahead, where our identity, content, and digital presence can be weaponized.
In this new era, where the incoming administration has been clear about their eager desire to go after their "enemies" and to stop "woke" organizations, we have all become "at risk" populations on the internet. Big Tech intentionally does not educate the public on how it's manipulating it's products to profit off of us. That's where we can become more curious and aware of our tech use and footprint.
Re-Assessing the Landscape in Troubled Times
There is a long history of authoritarian actors using digital surveillance. I recommend 'Dark Matters: On the Surveillance of Blackness' by Simone Browne to learn about the origins. Like the history of the police itself, its origins are tied to the control of Black bodies and the need to secure property for white elites.
The same thing has happened in the digital frontier. The slow creep of surveillance through advertising and other profit-driving solutions has led to a privatized Internet where one corporation controls the welcome mat (Google Search), its frenemies erect high digital walls to keep people hanging out only in their gardens (Meta, TikTok), and a new player is stealing any intellectual or creative artifact it can find (ChatGPT)!
Internet privacy and security are in the past for the foreseeable future so we as individuals need to rethink the landscape that we think we're used to so that we can be more discerning on how we choose our tech.
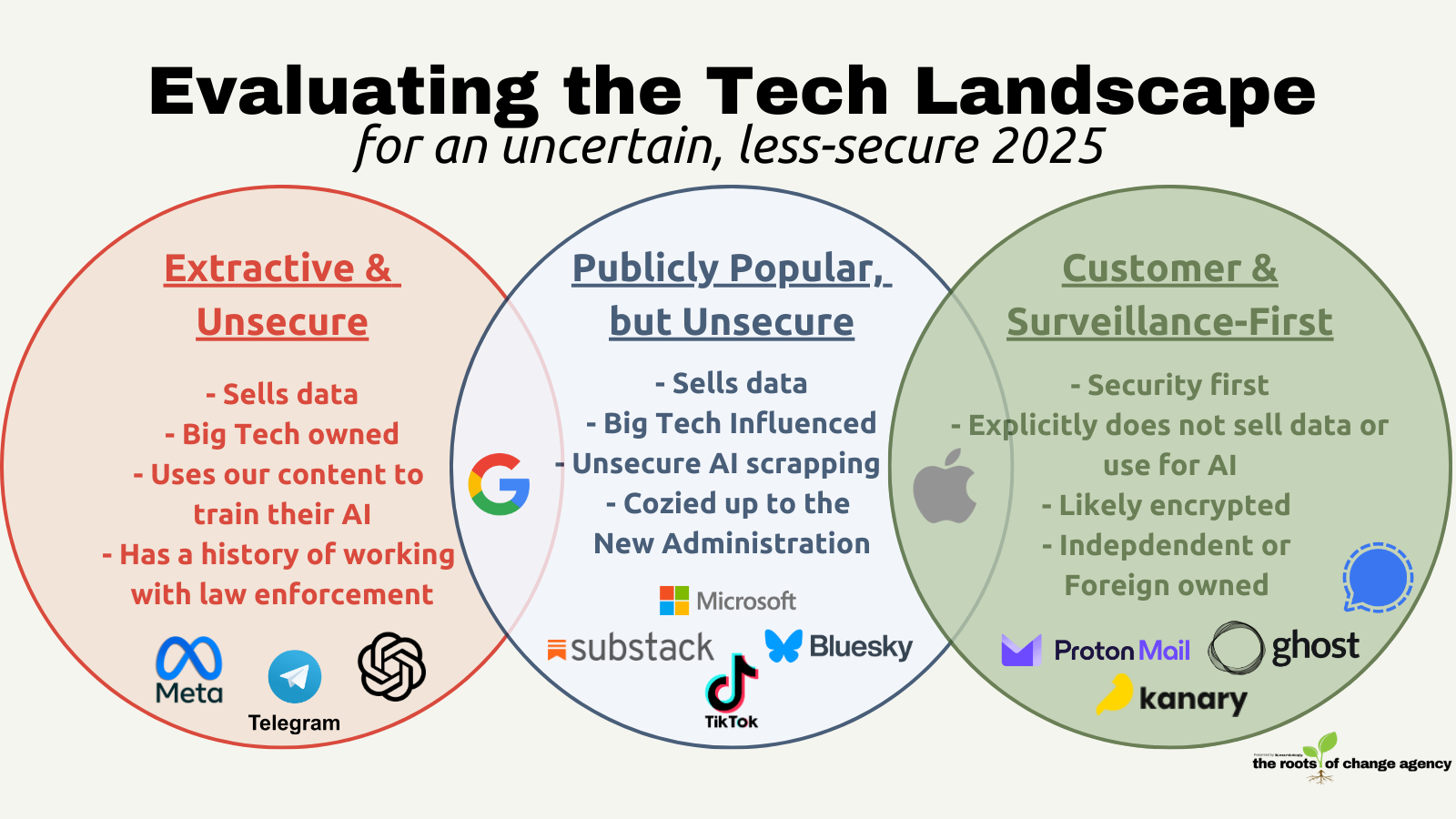
Ever since the election happened, I’ve had this image in my head of the different spheres of tech privacy. It’s been a way for me to sort through my own tech decisions and make sense of the shifting landscape especially with the government's statements that they will weaponize access. The rapid shifts have often felt topsy turvy. My own views on TikTok's privacy helps to illustrate just how much the landscape has shifted.
Before the pandemic, I was vehemently against joining TikTok, because I did not want China to have my data. Over time, China has proven to be just as trustworthy with my data as the major U.S.-based tech giants…that is to say, completely untrustworthy. I did end up joining TikTok, but mostly because I recognized I was compromised more on U.S.-based apps. Since then, I think of my tech in three spheres with TikTok landing in the middle as unsafe tech, but a place where people are.
As communicators (or Ariel), we do need to be where the people are so that we can connect and persuade. Considering tech in these 3 spheres helps to make strategic decisions on what I want to say on more secure platforms like this newsletter vs. a public platform like Instagram or LinkedIn. Knowing that they are unsecure doesn't mean that I won't be on there, it just means that I'll be more discerning.
Questions for evaluating tech
Speaking of! These are the questions that I ask myself when evaluating my digital footprint and spaces I want to be in.
- Is it Big-Tech owned? (assess if profit-motive is the only focus)
- Is it based in the U.S.? (how much government control)
- Do they sell user data or use it for other services?
- Do they use user content to train AI?
- Do they allow data scrapping or lax in stopping data scrapping?
- Do they have a history working with law enforcement?
- Do they say they're secure?
- Does the cyber security community like it? (are they actually secure?)
Over the next week, take some time to think through the apps and websites that you regularly use. Review the evaluation questions to interrogate your current relationship with tech and how you would like to transform it for 2025.
Next week, we’ll keep building upon that thinking with step-by-step tips on securing your identity and content online. Then in our final week of the year, we’ll close with building a resilient tech stack for yourself and organizations!
This post is for subscribers only
SubscribeAlready have an account? Log in


